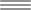High-level flow
LE is ELIoT Pro’s low compute and low power resource solution to the limitations of many of today’s IoT environments. Current and future IoT applications increasingly use simple battery-powered sensors and actuators, so encryption and M2M authentication must accommodate extremely low power and constrained computational device capabilities. To date, the small processor size limits and low clock speeds typically encountered in IoT implementations combined with limited battery power have greatly limited encryption and authentication options available to the IoT industry. Public key infrastructure computational requirements are an obstacle to the creation of cybersecurity solutions for the IoT industry, consequently, a different approach has to be followed to define lightweight, high-security encryption and authentication protocols. LE was formulated, built, and tested to satisfy the key requirements of being a computationally light, low memory use cipher that is both simple and highly secure. The binary substitution Vernam based approach to LE does not rely on polynomial computing normally used for prime number-based operations in modern encryption algorithms. This has the advantage of creating a fast and low CPU usage approach to encryption operations while eliminating vulnerability to computationally intensive brute force attacks. These types of attacks render conventional encryption methodologies vulnerable but are ineffective against LE because LE does not encrypt using mathematical operations. In the coming age of Quantum Computing, compute-intensive brute force attacks are of great concern for the cryptographic community, and ciphers resistant to these attacks are in high demand.
The LE key generation algorithm, operating on both ends of the LE transmission link, produces a two-peer blockchain implementation wherein both peers contain a type of one-way hash of all preceding communications between a pair of devices. This creates a pair of entangled peer transmission points. The result is a secure communication flow between peers, which continuously authenticates both sides of the transmission via a continuous and growing entanglement of device peers. In this manner, LE is able to secure IoT data transmissions while it authenticates IoT devices on its network.