Overview
Let’s assume the following client architecture. From some IoT devices, telemetry is being passed to IoT Hub and later is fetched by some other client-defined application (in this case some virtual machine, with IoT Edge Device included) and later passed along to some other processing service.
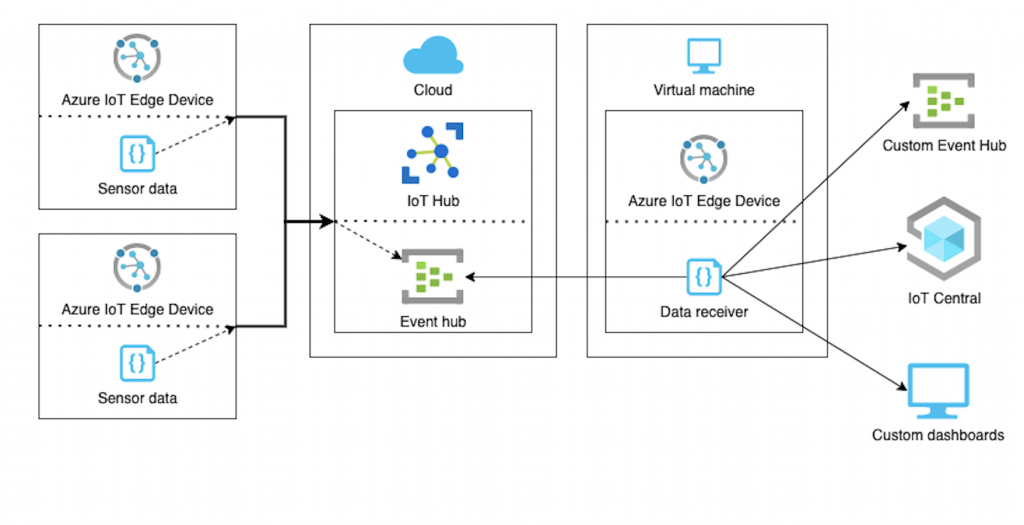
The payload of telemetry from leaf devices up to the end processing device is unencrypted and can be visible by anyone with reading permission to the Event Hub. Or in the context of more elaborate infrastructures, even more in between nods will have access to that data.
The solution to that is adding some encryption to the start and end-device of the processing flow.
Hence, the Lightweight Encryption IoT Edge module comes…
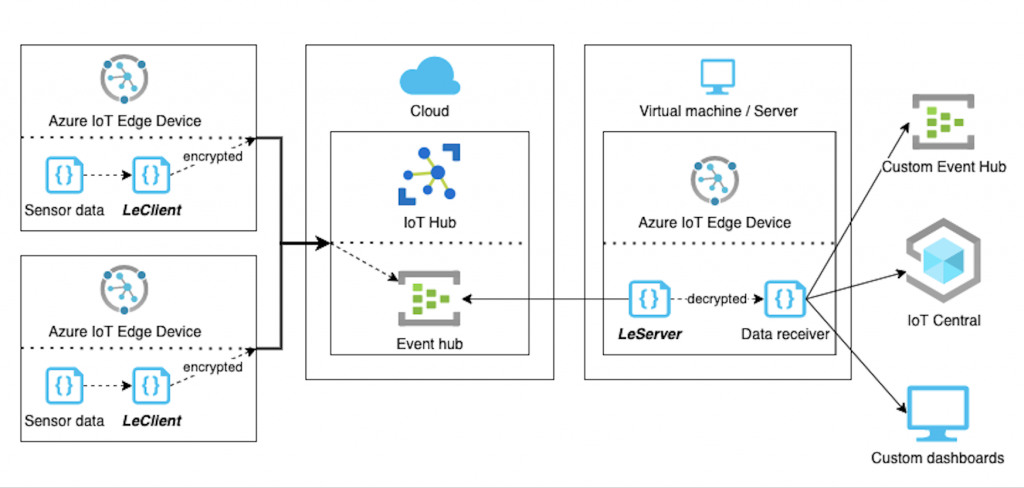
Now all the data passing through the Lightweight Encryption Client (LeClient) module will be encrypted up to the point of being decrypted on the Lightweight Encryption Server (LeServer) module.
Later it can be passed along to either upstream, another event-hub, or simply to another IoT Edge Module.