Enhancing Security at IoT World ICS Cybersecurity Day 2024 | Cyberus Labs’ Lightweight Encryption for ICS
Published November 1, 2024
See our founder, Jack Wolosewicz, alongside cybersecurity veterans at IoT World ICS Cybersecurity Day 2024 to learn about today’s IIoT threats, regulations and compliance and how Cyberus Labs’ patented IoT cybersecurity suite with its lightweight encryption technology can best secure industrial control systems and vital community infrastructure. In today’s connected world, securing industrial control systems (ICS) and community infrastructure is paramount. At IoT World
More
Katowice, Poland Pioneers Ground-Breaking Steps to Protect Smart-City Infrastructure Systems and Citizens from Cybersecurity Attacks by Deploying ELIoT Pro by Cyberus Labs, the World’s First End to End Internet of Things (IoT) Protection Platform, Featuring Downloadable Lightweight Encryption Technology.
Published March 7, 2022
Cyberus Labs is proud to announce that it has reached the next significant step in its partnership with the City of Katowice, Poland in protecting smart sensors and eventually primary infrastructure systems such as water delivery networks, public transportation, and power grids. “After the successful pilot implementation of our IoT cybersecurity solution ELIoT Pro , our team
More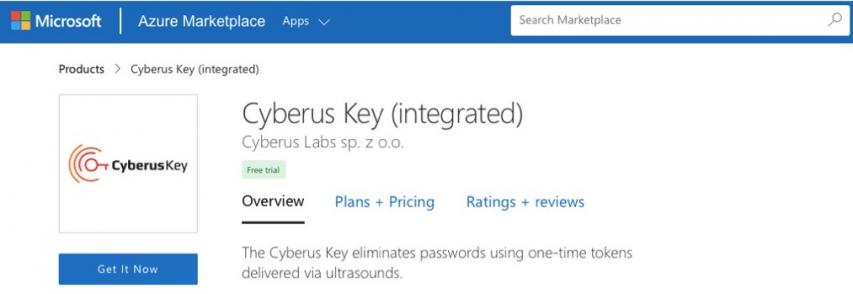
Cyberus Key Now Available in the Microsoft Azure Marketplace
Published July 1, 2021
Microsoft Azure customers worldwide now gain access to Cyberus Key to take advantage of the scalability, reliability, and agility of Azure to drive application development and shape business strategies. Katowice, Poland, European Union — July 1, 2021 Cyberus Labs Sp z o.o. today announced the availability of Cyberus Key in the Microsoft Azure Marketplace, an
More
Cyberus Labs joins the Art + Technology initiative to secure digitisation of the art world.
Published November 10, 2020
PRESS RELEASE Paris, France, November 10th, 2020 Cyberus Labs is excited to announce its participation in the most needed initiative by Convelio dedicated to support the art world in digitisation of its work and presence – Art + Technology. It is a consortium of some of the most innovative companies that will provide services and
More
Silicon Valley influence – Our approach to running the company | #Ep 15
Published June 1, 2020
This #15 episode unveils the mystery that has formed Cyberus Labs’ philosophy. It was the Silicon Valley that shaped it the way it is now, going in line with the saying “think outside of the box.” As a result we took a look how to avoid certain problems rather than tackling them. By bypassing them,
More
Cyberus Labs concludes the European Commission founded ELIoT Pro project.
Published May 29, 2020
Press release Katowice, May 29th, 2020 Cyberus Labs after completing its last technical deliverable due as part of the European Commission’s SME Instrument /Horizon 2020 programme has concluded two-years long journey. The result of it was development and preparation for commercialization of the breakthrough, end-to-end cybersecurity solution for IoT networks – ELIoT Pro. ELIoT Pro
More
ELIoT Pro reaching its final technology milestone, delivering IoT device provisioning component with use of the mobile app.
Published May 28, 2020
Press release Katowice, May 28th, 2020 Cyberus Labs has completed its last deliverable due as part of the European Commission’s SME Instrument /Horizon 2020 programme, which provides ELIoT Pro’s functionality of the IoT devices provisioning with the mobile app. In this last deliverable, we have enriched the ELIoT Pro platform with two new features. The
More
ELIoT Pro White Paper Series Part 4: Stay ahead of the hack
Published May 27, 2020
This whitepaper is the last of the 4 series of whitepapers that deal with cyber security. In this part, we answer the question ELIot Pro’s self-healing technology with predictive analytics works. We also write about how to keep system safe and secure. As you already known from the ELIoT Pro White Paper 3, Cyberus Labs
More
Enigma Part 2 – Why Enigma code was broken by Polish mathematicians | #Ep 14
Published May 25, 2020
Why did Polish mathematicians figure out how Enigma worked? This is the question which Jack Wolosewicz starts off episode 14. He is pointing out two main reasons. First, there has been a long academic tradition and history in Poland; high standards for intellectual accomplishments and understanding science and mathematics. One of the most outstanding examples,
More
Enigma Part 1: German Enigma’s encryption and its major weaknesses | #13
Published May 22, 2020
To begin with, Jack sheds light on the problem with the famous German coding machine Enigma used extensively during World War II by the German military. Its weakest part was human factor, as he explains. This, in turn, is essential in Human-to-Machine authentication nowadays. Therefore, human error of iterating the same message while sending encoded
More